In the beginning, the development of networks was chaotic. Each vendor had its proprietary solution. The bad part was that one vendor’s solution was not compatible with another vendor’s solution. This is where the idea for the OSI model was born. Having a layered approach to networks, our hardware vendors would design hardware for the network, and others could develop software for the application layer. Using an open model which everyone agrees on means we can build networks that are compatible with each other.
To fix this problem, the International Organization for Standardization (ISO) researched different network models, and the result is the OSI-model which was released in 1984. Nowadays, most vendors build networks based on the OSI model, and hardware from different vendors is compatible….excellent!
The OSI model isn’t just a model to make networks compatible; it’s also one of the BEST ways to teach people about networks. Keep this in mind since when you are studying networking, you will see people refer a lot to the OSI model.
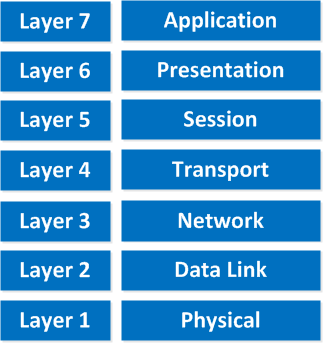
Here’s what the OSI model looks like:

“All People Seem To Need Data Processing”
This is the OSI model, which has seven layers; we work our way from the bottom to the top. Let’s start at the physical layer:
I’m taking a short break here, these four layers that I just described are important for networking, and the upper three layers are about applications.
“People Do Need To See Pamela Anderson”
This one normally gives me more smiles when I’m teaching CCNA in class, and it’s another way to remember the OSI-Model.
P = Physical
D = Data Link
N = Network
T = Transport
S = Session
P = Presentation
A = Application
Remember that you can’t skip any layers in the OSI model. It’s impossible to jump from the Application layer directly to the Network layer. You must always go through all the layers to send data over the network.
Let’s take a look at a real-life example of data transmission:
Once again, you cannot “skip” any layers of the OSI model. You always have to work your way through ALL layers. If you want a real-life story converted to networking land, just think about the postal service:
If you put your letter directly in the mailbox, it won’t be delivered. Unless someone at the postal office is friendly enough to deliver it anyway, in network land it doesn’t work this way! Going from the application layer all the way down to the physical layer is what we call encapsulation. Going from the physical layer and working your way up to the application layer is called de-encapsulation.
Now you know about the OSI model, the different layers, and the function of each layer. During peer-to-peer communication, each layer has “packets of information.” We call these protocol data units (PDU). Now every unit has a different name on the different layers:
This is just terminology, so don’t mix up talking about IP frames and Ethernet packets…
All this talk about layers is nice and all, but what about some action? We can see the different layers of the OSI model in action if we capture our network traffic on our computer.
Wireshark is a network capture tool that allows us to capture all packets we receive/transmit on our computer, and we can look at them.
Once you have downloaded and installed Wireshark, select the “Options” in the Capture menu:
You will now see an overview of all your network cards:
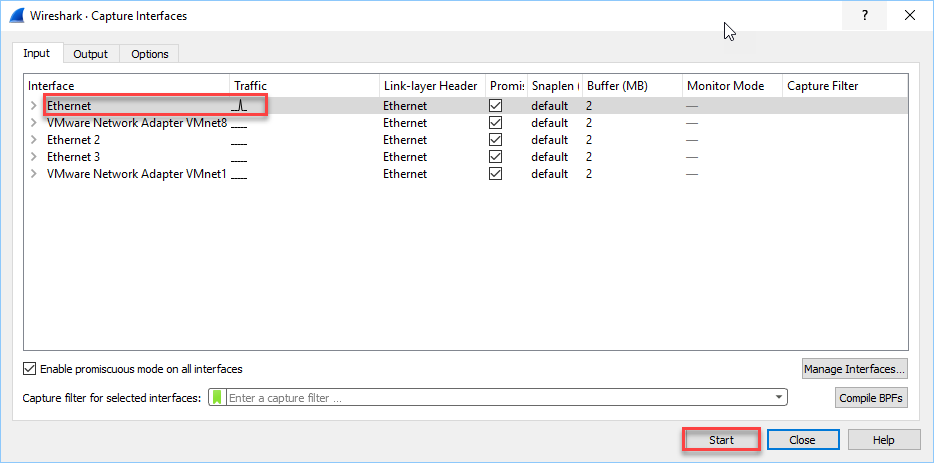
In my case, it’s the Ethernet interface that I want to capture. Hit Start, and it will capture all packets entering and exiting this interface. It will look like this:
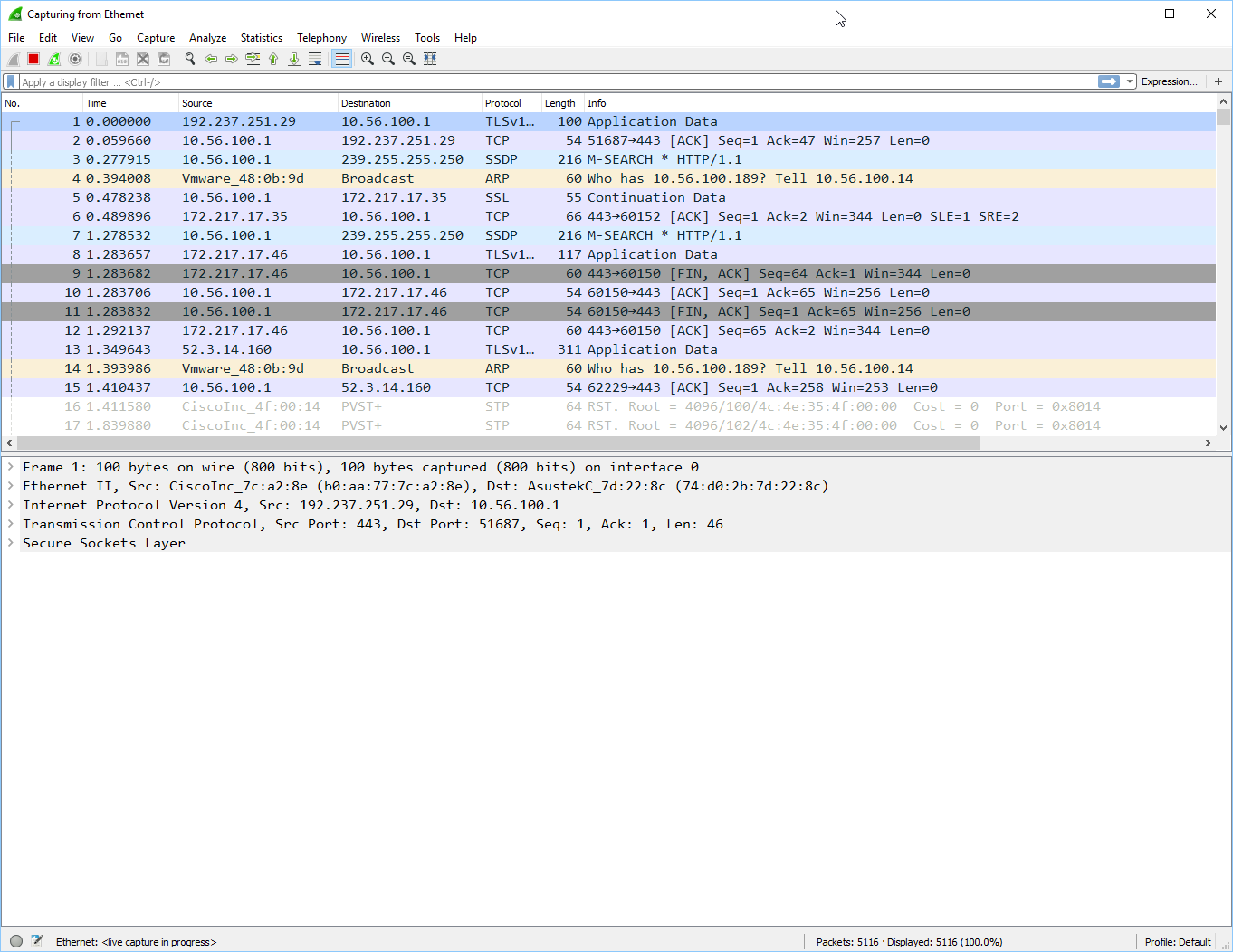
You will see a lot of stuff, don’t worry about what you see here. As you learn more about networking, you will also learn more about the different networking protocols and their packets/frames. We will capture one single frame and take a closer look at it. To do this, we will use a filter so that Wireshark only shows this traffic:
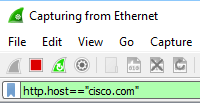
In the green bar on the top left, enter the following filter:
http.host=="cisco.com"Now open your web browser and open http://cisco.com.
Make sure you type http://cisco.com and not only cisco.com. Most websites use HTTPS by default which is encrypted.
Once the website has loaded, take a look at Wireshark:
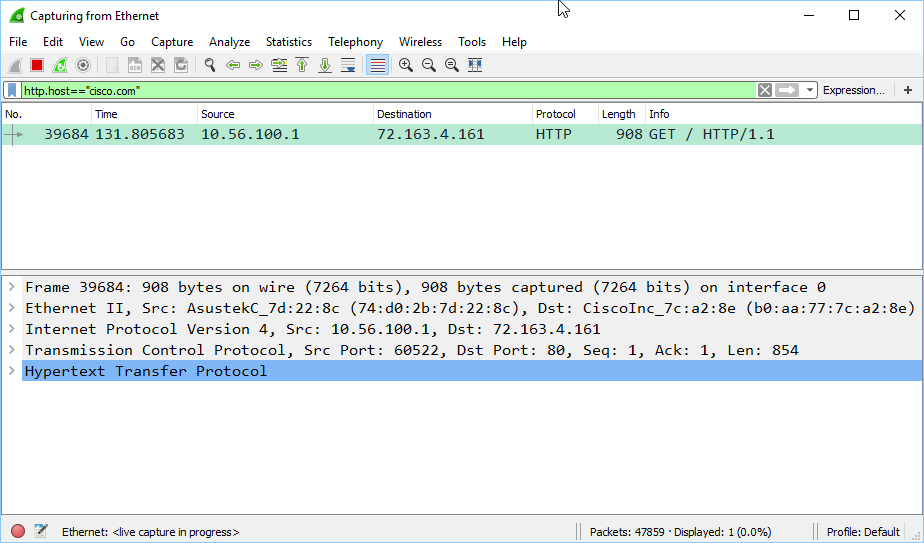
A single packet will show up with the request from our browser to fetch the Cisco.com website. At the bottom half of the screen, we can take a look at the contents of this frame. Let me break it down for you:
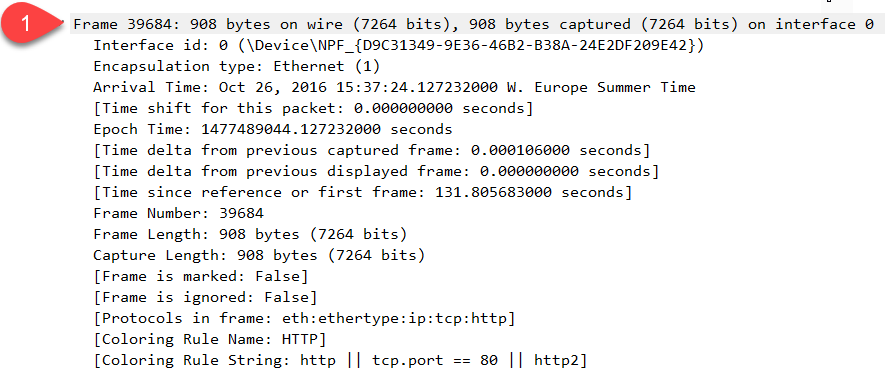
Wireshark has added the first piece of information. It tells us that we received an Ethernet frame that is 908 bytes. It also shows the arrival time. Here’s the second part:

Above we see layer two of the OSI model. This is the Ethernet frame, and it shows the source and destination MAC addresses. It also tells us the type. In this case, our Ethernet frame contains an IPv4 packet. Let’s check it out:
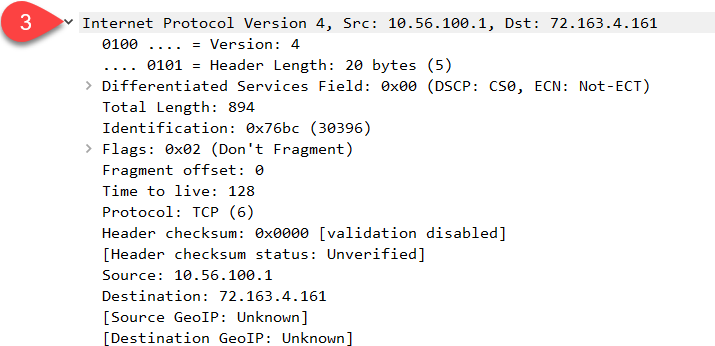
Above, we see the IP packet. This is layer three of the OSI model. Don’t worry about all the different fields here, we will cover it later. Two things you can recognize at the top are the source and destination IP addresses. Let’s continue:
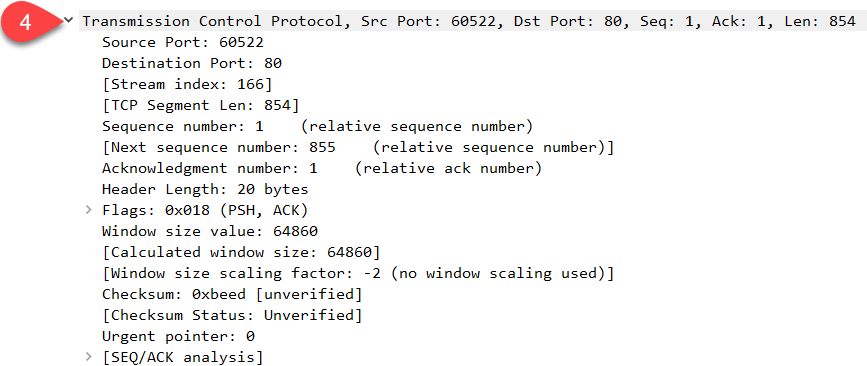
Above we see layer four of the OSI model. We are using TCP as the transport protocol here (which we will discuss later in detail). Last but not least, the last layer of the OSI model:
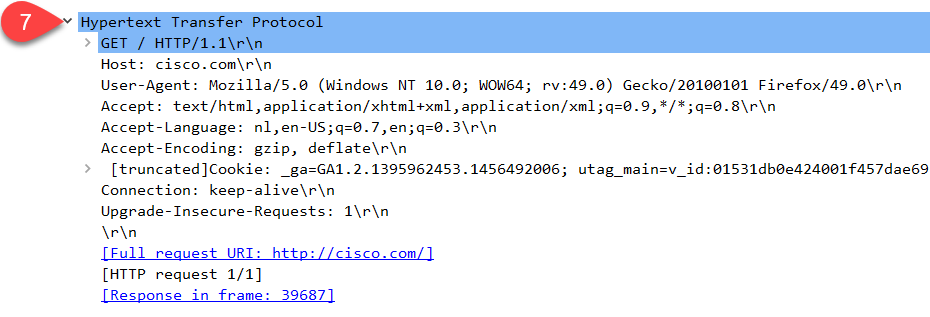
Above, you see layer seven, the application layer. Note that you don’t see a separate session and/or presentation layer here. You can see some information about the HTTP protocol here. We used a GET request to fetch cisco.com; the user agent I used was Mozilla (Firefox).
Want to take a look at this yourself? You can download my capture file:
You have now learned about the OSI model and its different layers. You have also seen how this applies to the real world with a packet capture in Wireshark. In other lessons, you will see that we use Wireshark quite often to look at different networking protocols and their inner workings.